How To Create A Risk Treatment Plan According to ISO 27001
- Alan Parker

- Sep 23, 2024
- 9 min read
Creating an ISO 27001 Risk Treatment Plan might seem daunting at first, but with the right approach, it becomes manageable and even rewarding.
In this guide, I’ll walk you through the steps to develop a robust Risk Treatment Plan that meets ISO 27001 standards and incorporates a comprehensive risk assessment process to strengthen your organisation’s information security posture.
Understanding the ISO 27001 Risk Management Process
The ISO 27001 risk management process is a cornerstone of the ISO 27001 standard. It provides a structured framework for managing and reducing risks to your organisation’s information assets. This process ensures that risks are identified, assessed, and treated in alignment with your organisation’s risk management strategy.
Understanding the Risk Treatment Plan
A Risk Treatment Plan is a documented approach to managing the risks identified during your risk assessment. It outlines how your organisation intends to treat each risk by mitigating, transferring, accepting, or avoiding it.
The treatment plan is a critical component of the ISO 27001 Information Security Management System (ISMS) and serves as a roadmap for implementing security controls by utilising various risk treatment strategies.
Why Is It Important?
The Risk Treatment Plan bridges the gap between knowing your risks and taking action to address them. It ensures that every identified risk has a clear strategy and responsible parties assigned to it. This not only helps in achieving ISO 27001 compliance but also fosters a proactive security culture within your organisation.
Starting with a Risk Assessment
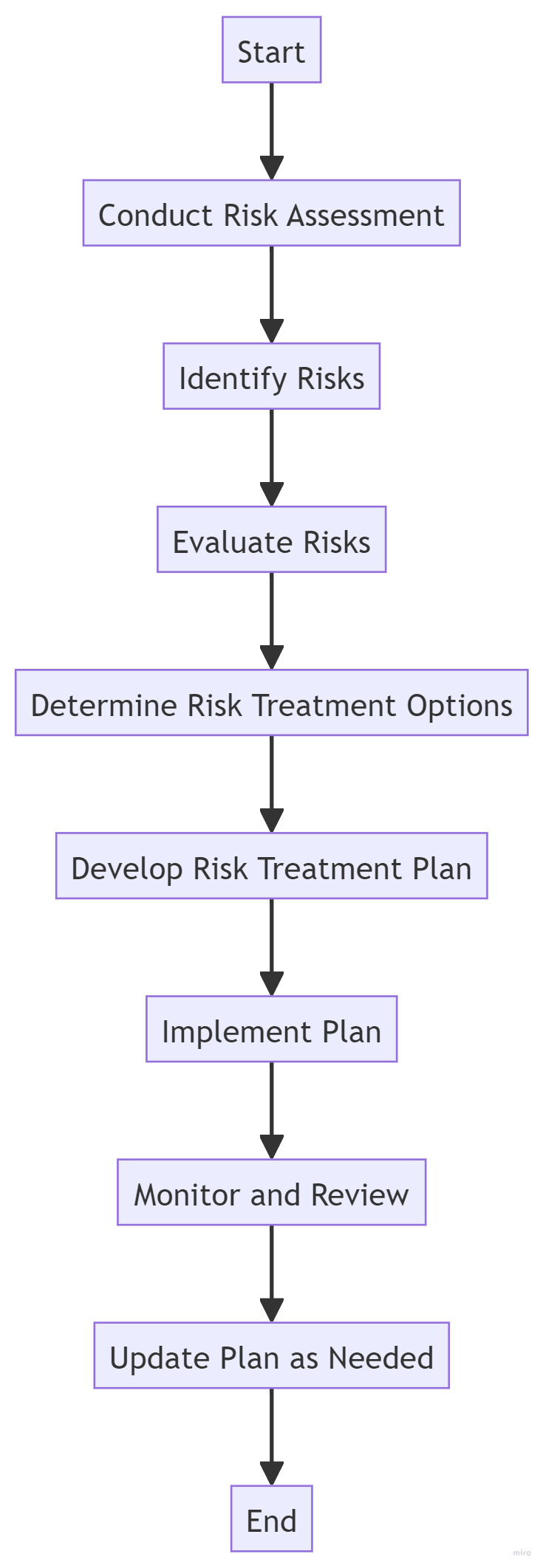
Before you can treat risks, you need to know what they are. A thorough risk assessment is the foundation of your Risk Treatment Plan. It involves risk identification, identifying assets, threats, vulnerabilities, and the potential impact on your organisation.
Steps in Conducting a Risk Assessment
Asset Identification: List all assets, such as hardware, software, data, and personnel, that could be affected by security threats.
Threat Identification: Identify potential threats to each asset, like cyber-attacks, natural disasters, or human error.
Vulnerability Assessment: Determine the vulnerabilities that these threats could exploit.
Impact Analysis: Evaluate the potential impact on your organisation if a vulnerability is exploited.
Risk Evaluation: Assign risk levels based on the likelihood of occurrence and the severity of impact.
I recommend using a risk assessment matrix to quantify and prioritise risks effectively.
Identifying Risk Treatment Options
Once you’ve identified and evaluated the risks, the next step is to decide how to treat them. The most common risk treatment option is risk reduction, which encompasses strategies to minimise the impact of potential risks. ISO 27001 provides four risk treatment options:
Risk Avoidance: Eliminating the risk by removing the cause.
Risk Mitigation: Reducing the risk likelihood or impact through controls.
Risk Transfer: Shifting the risk to a third party, such as through insurance or outsourcing.
Risk Acceptance: Acknowledging the risk and accepting it without additional action.
Carefully consider each option’s feasibility and impact on your resources.
Selecting Appropriate Options
High-Risk Items: Typically require risk reduction through mitigation or avoidance due to their potential impact.
Medium-Risk Items: Depending on cost-benefit analyses, these may be mitigated or transferred.
Low-Risk Items: Might be accepted if the cost of treatment outweighs the benefits.
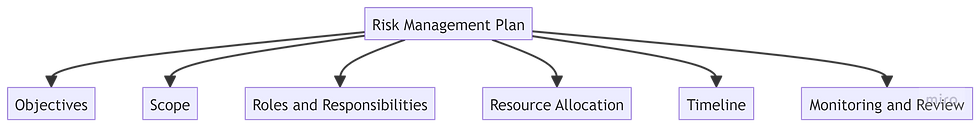
Developing the Risk Management Plan
Your Risk Treatment Plan doesn't exist in isolation; it's part of a broader Risk Management Plan. This plan outlines the overall risk management strategy and includes policies, procedures, and assigned responsibilities.
Key Elements to Include
Objectives: Define what the plan aims to achieve in line with your organisation's goals.
Scope: Specify the areas, departments, or systems the plan covers.
Roles and Responsibilities: Assign tasks to specific individuals or teams.
Resource Allocation: Identify the resources needed for implementation.
Timeline: Set realistic deadlines for each action item.
Monitoring and Review: Establish processes for ongoing assessment and updates.
I recommend integrating the Risk Management Plan into your organisation's strategic planning to ensure alignment and commitment.
How to Create a Risk Treatment Plan
Now that you have all the pieces let's assemble them to form a cohesive risk treatment plan.
Step-by-Step Guide
Consolidate Risk Assessment Findings: Gather all the data from your risk assessment, focusing on high-priority risks.
Define Treatment Actions: Decide on the risk treatment option and outline specific actions for each risk.
Example: The treatment action might be implementing multi-factor authentication for a risk of unauthorised access.
Assign Responsibilities: Allocate each action to a responsible party or team.
Set Deadlines: Establish realistic timelines for the completion of each action.
Determine Resources: Identify the budget, tools, and personnel required.
Develop Control Measures: Specify the security controls that will mitigate the risks.
Document Everything: Ensure all the details are recorded in a structured format.
Review and Approval: Have the plan reviewed by stakeholders and obtain necessary approvals.
Implement the Plan: Execute the actions as per the schedule.
Monitor Progress: Regularly check the status of each action item and adjust as needed.
Tips and Recommendations
Involve Stakeholders: Involve key stakeholders early to gain buy-in and diverse perspectives.
Prioritise Actions: Focus on high-impact risks first to maximise your efforts.
Be Realistic: Set achievable goals and timelines to maintain momentum.
Continuous Improvement: Treat the plan as a living document that evolves with your organisation.
Implementing the Risk Treatment Plan
Implementing a risk treatment plan is pivotal in the ISO 27001 risk management process. This plan should be tailored to your organisation’s needs and include several key elements to ensure effectiveness.
Practical Steps for Implementation
Implementing a risk treatment plan requires a structured and methodical approach. Here are some practical steps to guide you through the process:
Develop a Risk Treatment Plan Template: Create a template that includes all the key elements described above. Tailor this template to fit your organisation’s specific needs and risk profile.
Identify and Assess Risks: Use a risk assessment methodology, such as ISO 27005, to identify and assess the risks to your information assets. This step ensures that all potential risks are thoroughly evaluated.
Select Controls: Choose appropriate controls to mitigate or manage the identified risks. Utilise a control selection methodology, such as ISO 27002, to ensure the controls are effective and aligned with best practices.
Implement Controls: Follow the implementation plan to implement the selected controls. Ensure all necessary resources, including budget and personnel, are allocated to support the implementation.
Monitor and Review: Continuously monitor and review the effectiveness of the controls. Update the risk treatment plan as necessary to address any changes in the risk landscape or the effectiveness of the controls.
By following these practical steps, you can ensure that your risk treatment plans are effective, aligned with ISO 27001 standards, and capable of mitigating risks to your organisation’s information assets.
Maintaining and Updating the Plan
Creating the plan is just the beginning. Ongoing maintenance ensures its effectiveness over time.
Regular Reviews
Schedule periodic reviews of the Risk Treatment Plan to assess progress and make necessary adjustments. Depending on your organisation's needs, this could be quarterly, semi-annually, or annually.
Incident Feedback
Incorporate lessons learned from security incidents into your plan. This proactive approach helps prevent future occurrences.
Stay Informed
Keep abreast of new threats, vulnerabilities, and best practices in information security. Adjust your plan accordingly to address emerging risks.
Q&A Section
Q1: What is the main purpose of a Risk Treatment Plan in ISO 27001?
A: The main purpose of a Risk Treatment Plan is to outline how your organisation intends to manage the information security risks identified during the risk assessment. It specifies the chosen risk treatment options for each risk, the actions to be taken, responsible parties, timelines, and resources required. This plan serves as a roadmap to mitigate risks and achieve compliance with ISO 27001.
Q2: How does a Risk Treatment Plan differ from a Risk Assessment?
A: A Risk Assessment identifies, analyses, and evaluates risks to your organisation's information assets. It answers the question, "What are our risks?" On the other hand, a risk treatment plan addresses the following question: "What are we going to do about these risks?" It takes the findings from the risk assessment and outlines specific actions to manage or mitigate those risks.
Q3: What key components should be included in a Risk Treatment Plan?
A: I recommend including the following components in your Risk Treatment Plan:
Risk Description: A clear statement of each identified risk.
Risk Level: The assessed severity is based on likelihood and impact.
Treatment Option: The chosen method for handling the risk (avoid, mitigate, transfer, accept).
Action Plan: Specific steps to implement the treatment option.
Responsible Party: Individual or team accountable for executing the action plan.
Timeline: Deadlines for when actions should be completed.
Resources Needed: Budget, tools, and personnel required for implementation.
Q4: How often should the Risk Treatment Plan be updated?
A: I recommend reviewing and updating the Risk Treatment Plan regularly, at least annually, or whenever significant changes occur within the organisation. Changes could include new technologies, processes, personnel, or emerging threats. Regular updates ensure the plan remains effective and aligned with your organisation's risk landscape.
Q5: Can we accept certain risks instead of treating them?
A: Yes, risk acceptance is one of the risk treatment options in ISO 27001. If a risk falls within your organisation's risk appetite and the cost of mitigation outweighs the benefits, it may be acceptable to acknowledge the risk without additional action. However, this decision should be documented and justified within the Risk Treatment Plan.
Q6: What is the role of stakeholders in developing the Risk Treatment Plan?
A: Involving stakeholders is crucial for the plan's success. Stakeholders provide valuable insights into the risks and practicalities of implementing treatment options. I recommend engaging department heads, IT staff, security personnel, and even end-users during planning. Their input ensures the plan is comprehensive and that those responsible for execution are committed and informed.
Q7: How does the Risk Treatment Plan integrate with other ISO 27001 requirements?
A: The Risk Treatment Plan is interconnected with several ISO 27001 requirements:
Annex A Controls: The plan should map identified risks to relevant controls from Annex A.
Statement of Applicability (SoA): The SoA summarises which controls are applicable and how they are implemented based on the Risk Treatment Plan.
Continuous Improvement: The plan should feed into the Plan-Do-Check-Act (PDCA) cycle, promoting the ongoing enhancement of the ISMS.
Q8: What are some common challenges when creating a Risk Treatment Plan?
A: Common challenges include:
Resource Constraints: Limited budget or personnel can hinder implementation.
Risk Prioritisation: Difficulty in accurately assessing and prioritising risks.
Stakeholder Buy-in: Resistance or lack of support from key stakeholders.
Documentation: Ensuring all aspects are thoroughly documented for compliance.
I recommend addressing these challenges by securing management support, involving a cross-functional team, and employing clear communication.
Q9: Is it necessary to use specialised software for the Risk Treatment Plan?
A: While specialised risk management software can streamline the process, it's unnecessary. Smaller organisations might effectively use spreadsheets or document templates. The key is to ensure the plan is well-organised, accessible, and maintained. I recommend choosing a tool that fits your organisation's size, complexity, and resources.
Q10: How do we measure the effectiveness of the Risk Treatment Plan?
A: Effectiveness can be measured by:
Monitoring Key Performance Indicators (KPIs): These include the number of incidents before and after implementation.
Audit Findings: Internal or external audit results can highlight success or improvement areas.
Compliance Status: Achieving or maintaining ISO 27001 certification indicates effectiveness.
Stakeholder Feedback: Collecting input from those involved in executing the plan.
I recommend establishing clear metrics during the planning phase to evaluate progress over time.
Q11: What happens if a new risk emerges after the plan is in place?
A: New risks should be incorporated into the Risk Treatment Plan through the established monitoring and review process. I recommend updating the risk assessment and adjusting the plan to address the new risk, ensuring that your organisation remains proactive in its risk management efforts.
Q12: Can the Risk Treatment Plan be integrated with other management systems?
A: Yes, integrating the Risk Treatment Plan with other management systems like ISO 9001 (Quality Management) or ISO 22301 (Business Continuity) can provide a holistic approach to organisational risk. This integration fosters consistency, reduces duplication of efforts, and enhances overall efficiency. I recommend considering this integrated approach if multiple management systems are in place.
Conclusion
Developing an ISO 27001 Risk Treatment Plan is vital in safeguarding your organisation's information assets. By conducting a thorough risk assessment, identifying appropriate risk treatment options, and integrating them into a comprehensive risk management plan, you're setting a solid foundation for security and compliance.

Remember, the goal is to create a document for certification purposes and implement a practical strategy that enhances your organisation's resilience against threats. I recommend viewing this process as an opportunity to strengthen your operations and foster a culture of security awareness.
By following the steps outlined in this guide, you're well on your way to creating an effective Risk Treatment Plan that meets ISO 27001 standards and supports your organisation's long-term success.








留言